Articles in the HACKING FOR BEGINNERS Category
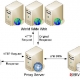
Proxy is a network computer that can serve as an intermediate for connection with other computers. They are usually used for the following purposes:
As firewall, a proxy protects the local network from outside access.
As IP-addresses …
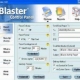
Keystroke loggers are stealth software that sits between keyboard hardware and the operating system, so that they can record every key stroke.
There are two types of keystroke loggers:
1. Software based and
2. Hardware based.
Spy ware: Spector …
A Trojan horse is an unauthorized program contained within a legitimate program. This unauthorized program performs functions unknown (and probably unwanted) by the user.
It is a legitimate program that has been altered by the placement …
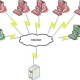
Its Real,On February 6th, 2000, Yahoo portal was shut down for 3 hours. Then retailer Buy.com Inc. (BUYX) was hit the next day, hours after going public. By that evening, eBay (EBAY), Amazon.com (AMZN), and …

The following are the IP utilities available in Windows that help in finding out the information about IP Hosts and domains.These are the basic IP Hacking Commands that everyone must know!
NOTE: The term Host used …
One of most the frequently asked question is how to track an email back to the sender.That is how to determine the sender of the email? The most obvious answer is by looking at the …




