Articles in the LEARN HACKING - FOR BEGINNERS category
Internet Protocol (IP) addresses are usually of two types: Public and Private. If you have ever wondered to know what is the difference between a public and a private IP address, then you are at the right place.
In …
CAPTCHA or Captcha (pronounced as cap-ch-uh) which stands for “Completely Automated Public Turing test to tell Computers and Humans Apart” is a type of challenge-response test to ensure that the response is only generated by humans …
Here is a DETAILED tutorial which contains every possible information that you need to know about keyloggers.
I know most of you are new to the concept of keyloggers. For some of you, this might be the first …
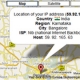
In my earlier post, I had discussed on How to find the IP address of a remote computer. But once you obtain this IP address, it is necessary to trace it back to the source. So, in …
Most of us are very curious to learn Hacking and want to become a Hacker, but don’t know where to start. If you are in a similar situation, then this article will most likely guide you to …

If you are a newbie in Internet security, you have come to the right place. The following is information on some common terms used in Internet security. So next time you don’t have to scratch …
Port Scanning is one of the most popular techniques used by hackers to discover services that can be compromised.
A potential target computer runs many ‘services’ that listen at ‘well-known’ ‘ports’.
By scanning which ports are available …
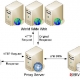
Proxy is a network computer that can serve as an intermediate for connection with other computers. They are usually used for the following purposes:
As firewall, a proxy protects the local network from outside access.
As IP-addresses …


 I am Srikanth Ramesh, a computer engineer from India.
I am Srikanth Ramesh, a computer engineer from India.